Career Reminiscing
- stop making its iconic black computers
- abandon work on a PowerPC-based workstation
- try selling its hardware business and factory to Canon
- focus on software
- rename the company "NeXT Software"
- lay off 300 of its 540 employees.
- there were no associates
-
Use “sndrecord ping.snd”, hit return, say the word “PING” into the mike, hit return again. Try to make the recording less than 1 second long.
-
Run this script
Apple + NeXT, 25 years ago today.
Remembering the merger of Apple and NeXT and how anxious we all were and how well it worked out. Also with a new baby.
Remembering NeXT's Black Monday. Or possibly Sunday.

NeXT's Black Monday
Today’s the 28th anniversary of the day in 1993 that NeXT decided to
and not insignificantly
Including me, Systems Engineer for NeXT Canada.
(Later on, of course, Apple purchased NeXT and its software became the core of iOS, macOS, watchOS and tvOS, all running on hardware that was inconceivable to any of us in 1993.)
or possibly Sunday
Looking back at my calendar I see that February 7, 1993 was actually a Sunday, so I might be off by one in my reminiscing. But still. It was kind of a big deal, personally.
vague reminiscences, previously tweeted
I remember we all got an urgent voice mail and the entire NeXT Canada office - all 3 of us - were instructed to fly to Chicago immediately for some news.
That was an interesting trip as Phil, Paul and myself debated exactly what was going on and who was going to be left standing. We knew that the regional manager was out.
And we all got let go, effective immediately, and - I still can’t believe we felt we needed to do this - we went to visit our big customers back in Toronto in person the following day to let them know what was going on.
You know those tables where they assign numerical values to various stress factors? Getting laid off was one thing but we had also (2) just bought a house and (3) were expecting child #1. I needed a bigger chart.
I remain, however, eternally grateful to Trimark Investment Management, one of our biggest NeXT customers, because when we visited them to tell them all of NeXT Canada had been let go, they said “Huh. That’s unfortunate …. Steve do you want to do some consulting for us?”
Thus began the historic short life of the consulting firm of Steve Hayman and Associates *
One thing I remember from the layoff meeting in Chicago, where somebody I had never met before told me I no longer had a job. “I want to keep my computer.”
— OK … what computer do you have?
(Changed the subject quickly. I think I actually had two computers.)
One other thing I remember. Consulting for Trimark, they had a fleet of NeXT computers, I had one at home, so I bought a portable SCSI hard drive to carry my work back and forth because how else were you supposed to do it in 1993
a ONE GIGABYTE SCSI hard drive. Massive! And it was only $1000!
Today for $1000, you’d get, what, 50 terabytes? 50,000 times as much? Storage is 1/50,000 th of what it was? How many other things are 50,000 times cheaper? That’s basically FREE now.
I know this will come as a surprise to nobody but Steve Hayman and Associates was not exactly a huge success. (I blame the associates, of course.)
18 months later, as NeXT pivoted to software, the regional team - from Michigan - came to Toronto to present to, I forget who exactly, some bank or something. They kindly invited the entire Steve Hayman and Associates team to attend.
Before the session started, the NeXT team said in a kind of off-hand way, “Hey Steve, how about you do the presentation?”
I guess in retrospect it was kind of an audition.
And, whaddya know, I guess NeXT saw (one of) the error(s) of its ways, and offered me a job again.
note: it is possible I am still telling the same jokes in presentations, because, you know, Object Oriented programming encourages re-use
So, miraculously, even though this day in February 1993 was a very stressful low point for me and hundreds of others, I was lucky enough to get drafted by NeXT a second time.
For a while, NeXT Canada was me in Toronto, and a guy in Vancouver (hi Scott.) We’d phone each other on Memorial Day, or July 4, or US Thanksgiving just to verify the other guy was actually in the office.
I still have a surprising quantity of NeXT business cards. I keep those with my SCSI cables. Hey, you never know.
Audio Ping at 30
Thirty years ago today I achieved my first mild dose of Internet fame, with this post to the old comp.sys.next Usenet newsgroup. Here’s the original post first - and let me tell you about what happened afterwards. Also it involves ducks.
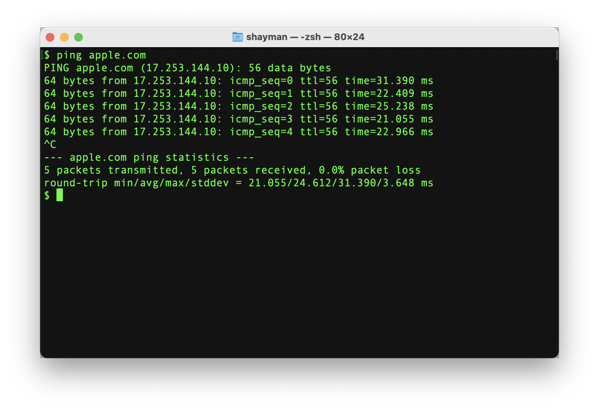
Date: Sun 23-Jan-1991 21:15:24 From: sahayman@iuvax.cs.indiana.edu (Steve Hayman) Subject: NeXT "audio ping" for network debuggingThe thinwire started messing up in the building where I work yesterday;
I was scurrying around with an ethernet terminator cutting off segments of the network to try to isolate where the problem was.I have a NeXT and a Sun on my desk, and was trying to ‘ping’ the Sun from the NeXT.
Whether it worked depended on where I cut the network off.ping is a good tool for debugging but it sure is a pain to have to run back to your office to see if any of the ping packets are getting through.
So I came up with this quick hack.
#!/bin/sh
audio-ping host
output of ‘ping’ looks like this:
# ping porbeagle
PING porbeagle.cs.indiana.edu: 56 data bytes
64 bytes from 129.79.254.138: icmp_seq=0. time=3. ms
64 bytes from 129.79.254.138: icmp_seq=1. time=3. ms
…
one line per second. no output is produced if the packets
aren’t coming back.
This script plays a sound whenever it sees a line with “icmp_seq” on it.
ping $1 2>&1 | while read line; do case “$line” in icmp_seq) sndplay ping.snd ;; esac done
Now start this up. Crank up the volume on your NeXT to the max.
You can now wander through the building fiddling with the network, unplugging different machines and so on; if it’s working you’ll hear this voice saying PING … PING … PING; if it quits working the voice will stop.If you wanted to get really fancy you could play a different sound for some of the other messages that ping might generate - sometimes ping says “network is down”, for instance.
This script helped me find a faulty tee-connector in just about a minute.
OK it’s a dumb hack.
Steve
ping? what's that?
ping is a Unix tool that attempts to make a connection to a remote computer, and once a second, it will print a line of received data. It’s a quick way to check if your network is working. Ping a faraway computer, and if you get a line of information back every second, your network is working.
I still use this today.
so what where you trying to do in 1991?

I was working for the computer science department at Indiana University - we’d temporarily been relocated to, I think, this building - while the main CS building was being renovated (and wow, did I ever wind up with a great office in the renovated building when it was done, Lindley Hall - corner office, top floor, overlooking the quad… and two weeks after we moved in, I quit to come back to Canada. I’ll never have an office like that again.)
Anyway. The network in our little house wasn’t working. I was running this ‘ping’ program and had to keep returning to my desk to see if it was working, as I experimented with changing network settings and futzing with cables on other computers in the building. We didn’t have portable computers, that’s for sure.
So what I did above was to combine the sound recording tool on my NeXT cube on my desk, with the Unix ping program, in a way that my computer would play a recording of me saying PING once a second when the network was working, and it’d be silent otherwise. I could then wander through the building adjusting things and when I heard the PING sound from upstairs, I knew I’d fixed it.
I didn’t think this was such a big deal but posted the above writeup to the net. A few people congratulated me.
and then what?
Somehow this little hack made it into the Jargon File, a legendary compilation of hacker terminology, and a subsequent book, The New Hacker’s Dictionary.. If you check the jargon file today, 30 years later, you can see this entry for ping-
ping [from the submariners' term for a sonar pulse] 1. n. Slang term for a small network message (ICMP ECHO) sent by a computer to check for the presence and alertness of another. The Unix command `ping(8)' can be used to do this manually (note that `ping(8)''s author denies the widespread folk etymology that the name was ever intended as acronym `Packet INternet Groper'). Occasionally used as a phone greeting. See ACK, also ENQ. 2. /vt./ To verify the presence of. 3. /vt./ To get the attention of. 4. /vt./ To send a message to all members of a mailing list requesting an ACK (in order to verify that everybody's addresses are reachable). "We haven't heard much of anything from Geoff, but he did respond with an ACK both times I pinged jargon-friends." 5. /n./ A quantum packet of happiness. People who are very happy tend to exude pings; furthermore, one can intentionally create pings and aim them at a needy party (e.g., a depressed person). This sense of ping may appear as an exclamation; "Ping!" (I'm happy; I am emitting a quantum of happiness; I have been struck by a quantum of happiness). The form "pingfulness", which is used to describe people who exude pings, also occurs. (In the standard abuse of language, "pingfulness" can also be used as an exclamation, in which case it's a much stronger exclamation than just "ping"!). Oppose blargh.The funniest use of
ping' to date was <strong>described in January 1991 by Steve Hayman</strong> on the Usenet group comp.sys.next. He was trying to isolate a faulty cable segment on a TCP/IP Ethernet hooked up to a NeXT machine, and got tired of having to run back to his console after each cabling tweak to see if the ping packets were getting through. So he used the sound-recording feature on the NeXT, then wrote a script that repeatedly invokedping(8)', listened for an echo, and played back the recording on each returned packet. Result? A program that caused the machine to repeat, over and over, “Ping … ping … ping …” as long as the network was up. He turned the volume to maximum, ferreted through the building with one ear cocked, and found a faulty tee connector in no time.
I gotta tell ya, to have your name mentioned in the Jargon File certainly gives you an aura of street cred in certain strange circles!
not only that

The Ping program itself was written by a legendary Unix developer at AT&T Bell Labs named Mike Muuss. He tragically passed away in a car accident in 2000 but his personal web site lives on, and I was delighted to see his page titled, The Story of the Ping Program.
He tells the interesting story of the birth of this program and then - much to my delight - includes this anecdote, which is mostly accurate
The best ping story I've ever heard was told to me at a USENIX conference, where a network administrator with an intermittent Ethernet had linked the ping program to his vocoder program, in essence writing:ping goodhost | sed -e 's/.*/ping/' | vocoderHe wired the vocoder’s output into his office stereo and turned up the volume as loud as he could stand. The computer sat there shouting “Ping, ping, ping…” once a second, and he wandered through the building wiggling Ethernet connectors until the sound stopped. And that’s how he found the intermittent failure.
Imagine my delight at stumbling across that, from the author of ping himself.
the best part
There’s a famous children’s book from 1933 called “The Story about Ping”. It’s about a duck, of course. A Duck! Ping, a spirited little duck who lives on a boat on the Yangtze River and gets into various misadventures. It’s about a duck. A duck named Ping.

But Mike Muuss’s page mentioned this legendary Amazon review of the book which still makes me laugh today.
Customer CommentsA reader from Upper Volta, Uzbekistan, March 7, 1999
Excellent, heart-warming tale of exploration and discovery. Using deft allegory, the authors have provided an insightful and intuitive explanation of one of Unix’s most venerable networking utilities. Even more stunning is that they were clearly working with a very early beta of the program, as their book first appeared in 1933, years (decades!) before the operating system and network infrastructure were finalized.
The book describes networking in terms even a child could understand, choosing to anthropomorphize the underlying packet structure. The ping packet is described as a duck, who, with other packets (more ducks), spends a certain period of time on the host machine (the wise-eyed boat). At the same time each day (I suspect this is scheduled under cron), the little packets (ducks) exit the host (boat) by way of a bridge (a bridge). From the bridge, the packets travel onto the internet (here embodied by the Yangtze River).
The title character – er, packet, is called Ping. Ping meanders around the river before being received by another host (another boat). He spends a brief time on the other boat, but eventually returns to his original host machine (the wise-eyed boat) somewhat the worse for wear.
The book avoids many of the cliches one might expect. For example, with a story set on a river, the authors might have sunk to using that tired old plot device: the flood ping. The authors deftly avoid this.
Who Should Buy This Book
If you need a good, high-level overview of the ping utility, this is the book. I can’t recommend it for most managers, as the technical aspects may be too overwhelming and the basic concepts too daunting.
Problems With This Book As good as it is, The Story About Ping is not without its faults. There is no index, and though the ping(8) man pages cover the command line options well enough, some review of them seems to be in order. Likewise, in a book solely about Ping, I would have expected a more detailed overview of the ICMP packet structure.
But even with these problems, The Story About Ping has earned a place on my bookshelf, right between Stevens' Advanced Programming in the Unix Environment, and my dog-eared copy of Dante’s seminal work on MS Windows, Inferno. Who can read that passage on the Windows API (“Obscure, profound it was, and nebulous, So that by fixing on its depths my sight – Nothing whatever I discerned therein."), without shaking their head with deep understanding. But I digress.
Rejoining the Breakpoints after 17 years
So I played in a band at the legendary Ritz in San Jose, California last night.
(below are some of the many great photos of the event by Adam Tow)


The whole event reminded me that it’s not really important how good a musician you are; you should just get together with your friends and play some music. (And maybe people will come! And they did, in this case; the event was a fundraiser for App Camp for Girls )
Wait, whaaat? What band are you in NOW? I thought the whole football band thing was over. Well, yeah it still is. This time I sat in with James  Dempsey and the Breakpoints at their 8th annual Live Near WWDC concert.
Dempsey and the Breakpoints at their 8th annual Live Near WWDC concert.
This is an annual concert put on by people attending Apple’s World Wide Developer Conference, and it’s spearheaded by my friend James who has written an entire chart-topping album of funny songs celebrating various technical aspects of programming and you can of course listen to the whole album here.
The band featured a whole group of people who are stars in the Mac world - including Daniel Jalkut, author of MarsEdit, the blogging software I am typing in right now - and many other luminaries that I bet most of my friends outside the Mac world have never heard of. But I don’t care! It was great fun to be invited!
for instance
Here’s one of my favourite numbers - The Liki Song (Minawana Meika La’a Likiko)
It’s a little Hawaiian number with James on ukulele - and it’s about memory management. I have to admit, the first time I listened to it - while walking through an airport - I had no idea what the heck James was singing about. “Liki” ? “Mina wana meika la’a likiko”? What the heck? What is he talking about?
And finally it dawned on me - “Me no want to make a lot of leaky code.” That stopped me in my tracks in the airport; I had to sit down, I was laughing so hard. And this was the big closing number at the show, with 24 musicians on stage and the entire crowd singing along. What a treat. So many songs, so many different styles.
how'd this start?
James and I both worked at Apple ages ago - I still do - and both presented at WWDC many times. I distinctly remember one year when I was getting ready for my talk and Matt Firlik announced to me that James had written an original song about Fetch Specifications for his talk, and right then, I knew the best any of the rest of us could hope for was to give the 2nd best presentation.
For years afterwards, the word would get out that James’s WWDC session was almost over and, regardless of topic, people would suddenly arrive for the last 5 minutes to hear his latest song about localization or the perils of designated initializers or whatever else struck his fancy.
A year or two later in 2002, he wrote another song at the developer conference about memory management called Hold Me, Use Me, Release Me - and I knew I had to up my game, and brought my trombone on stage for my own session on WebObjects and I told the crowd that I’d written an original trombone solo about Key-Value Coding, which I hoped I’d have time to perform.
To the great relief of everyone, including me, I did not have time to perform this (nonexistent) solo. But there was some sort of community event that night and James was asked to reprise the Hold Me song, and, well I happened to be around and happened to have a trombone on hand and my arm was twisted ever so slightly so I played along on stage with James.
And that was the last time I did, until 17 years later.
(Ten years later, I was visiting Cathy’s mom at her home in a tiny community in northern New Brunswick and tweeted something about it, and about five minutes later, the phone rang - it was James. “Are you really in Jacquet River, New Brunswick?” he asked in amazement - because it turns out his wonderful father Wilbur lived there too! Small world.)
the breakpoints
James eventually struck out on his own and formed a band of various other members of the geek-Apple community - all very talented musicians - and called the group the Breakpoints. (A breakpoint is a term in software debugging for a location where you want the program to stop so you can see what’s going on.)
He actually wound up with enough material to release an entire album of funny programming songs songs which actually was the #1 comedy album on iTunes for a while (and, if I remember correctly, #1 overall album in Bulgaria).
I was lucky enough to be dubbed a “conditional breakpoint”, i.e. someone who played with the band only rarely.
For years James and his band did these wildly popular fundraisers called “Live Near WWDC”, and I always went, and always enjoyed it, and always secretly wanted to be up there on stage too.
the show
Last night was my chance. 17 years after first playing with James, I was invited back to play trombone on a couple of numbers, including a rockin' round of trading licks with awesome guitarist Jim Dalrymple, in a song which could only have been improved if I had not forgotten what key it was in part way through. (note: it was in “A”.)
I am saving this tweet -
You are amazing!
— Jim Dalrymple (@jdalrymple) June 6, 2019
Wow, was it fun. Over 20 different muisicians in the band - singers, guitarists, drummers, a violin! a cello! And a guy with a blue trombone having the time of his life.
Thank you James. And thanks for the selfie below which you actually took during the middle of my solo, which perhaps caused me to forget the key signature (note, again: “A”)
I hope I can do it again in 2036. Maybe sooner!

My name's on your iPhone
Really. Go find it. I’ll wait.
Couldn’t find it? Settings > General > About > Legal > Legal Notices. Scroll waaaaaaaay down. Eventually you’ll hit this -
update - in 2022 it’s in Settings > General > Legal and Regulatory > Legal Notices

That’s right, Steve Hayman of the Indiana University Computer Science Department.
What’s all that about?
In 1989 or so I was working at Indiana University as a network manager in the computer science department. We had a fleet of Apollo and Sun workstations, and one or two of these weird NeXT cube things, which I wound up getting to know pretty well but that’s another story.
University of California, Berkeley had a popular variant of the UNIX system, which we used at IU on our Suns, including the Sun 3/60 on my desk, that happened to be based extensively on AT&T’s System V.
Berkeley wanted to get rid of the AT&T parts so that they could make it truly open-source and unencumbered by the AT&T license restrictions, so they put out a call for volunteers to rewrite certain AT&T programs from scratch. (The rules were: you were allowed to study and run the original, and look at the man page, but you couldn’t look at the original AT&T source code.)
Along with many other people who were much better programmers than me, I volunteered, and they asked me to take a stab at rewriting /usr/games/bcd, which was a silly little program that took text and drew a fake punch card around it.
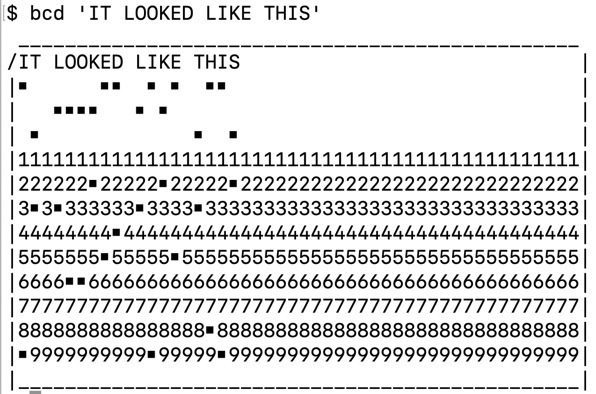
BCD stands for Binary Coded Decimal, which was the text encoding standard that evolved into EBCDIC (Extended Binary Coded Decimal Interchange Code), as used on punch cards, which I actually used in my first year Waterloo computing course on Fortran, and you would perhaps have liked the conference talk I gave at MacSysAdmin on the history of text encodings from Morse Code to Emoji - but more importantly - this bcd program qualified as high concept computer geek humor back in the day.
Also it was in /usr/games! What exciting computer games we had in those days!
AT&T Unix came with this utility, and I volunteered to rewrite it, and submitted the code to Berkeley.
They seemed happy with it and asked me to do another so I also rewrote /usr/bin/join, which is a sort of command line version of the database join function.
(That one was way more useful but way less fun to demo.)
Weirdly, the AT&T version only created 48-column cards instead of the standard 80-column card, but I was intent on copying the AT&T version, so if you ever look at the source you should change this line
int columns = 48;
So anyway I kind of forgot about it, but here we are, decades later.
Berkeley UNIX has continued to evolve, and a lot of the Berkeley code found its way into Linux, and MacOS, and even iOS.
Needless to say, iOS doesn’t actually include either the bcd or join programs, but it does include a lot of other Berkeley Unix code.
Apple lists the license agreement and credits for a ton of open source code in its Legal Notices section, and Berkeley, god bless them, has chosen to include the names of all these contributors from long ago. The Berkeley section says This code is derived from software contributed to Berkeley by …. and lists dozens of people, virtually all of whom did something way more important than I did.
But there it is. I’m sure hardly anybody reads the Legal Notices but it’s the first thing I check when there’s a new iOS release. Just making sure things are still there.
postscript
Berkeley unix mutated into OpenBSD and FreeBSD and NetBSD and Linux and MacOS and iOS and watchOS and tvOS and I can’t keep track of it all - but you can see the OpenBSD version of the BCD source here.
I am really amused that in my efforts to copy the AT&T version exactly, I inadvertently copied a bug from the original! Four years later, Dyane Bruce noticed (and fixed) that Q and R were being punched the same way! ooops.
My name's on your iPhone
Really. Go find it. I’ll wait.
Couldn’t find it? Settings > General > About > Legal > Legal Notices. Scroll waaaaaaaay down. Eventually you’ll hit this -

That’s right, Steve Hayman of the Indiana University Computer Science Department.
What’s all that about?
In 1989 or so I was working at Indiana University as a network manager in the computer science department. We had a fleet of Apollo and Sun workstations, and one or two of these weird NeXT cube things, which I wound up getting to know pretty well but that’s another story.
University of California, Berkeley had a popular variant of the UNIX system, which we used at IU on our Suns, including the Sun 3/60 on my desk, that happened to be based extensively on AT&T’s System V.
Berkeley wanted to get rid of the AT&T parts so that they could make it truly open-source and unencumbered by the AT&T license restrictions, so they put out a call for volunteers to rewrite certain AT&T programs from scratch. (The rules were: you were allowed to study and run the original, and look at the man page, but you couldn’t look at the original AT&T source code.)
Along with many other people who were much better programmers than me, I volunteered, and they asked me to take a stab at rewriting /usr/games/bcd, which was a silly little program that took text and drew a fake punch card around it.
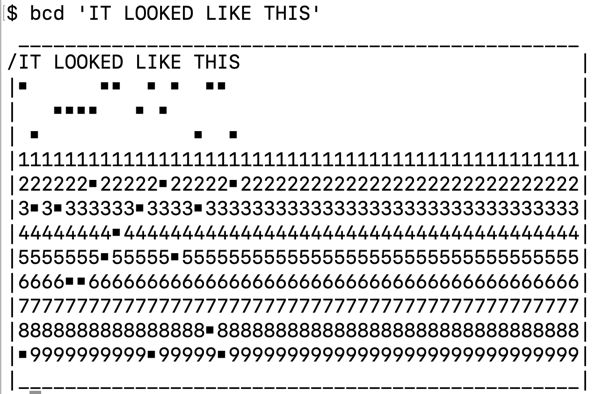
BCD stands for Binary Coded Decimal, which was the text encoding standard that evolved into EBCDIC (Extended Binary Coded Decimal Interchange Code), as used on punch cards, which I actually used in my first year Waterloo computing course on Fortran, and you would perhaps have liked the conference talk I gave at MacSysAdmin on the history of text encodings from Morse Code to Emoji - but more importantly - this bcd program qualified as high concept computer geek humor back in the day.
Also it was in /usr/games! What exciting computer games we had in those days!
AT&T Unix came with this utility, and I volunteered to rewrite it, and submitted the code to Berkeley.
They seemed happy with it and asked me to do another so I also rewrote /usr/bin/join, which is a sort of command line version of the database join function.
(That one was way more useful but way less fun to demo.)
Weirdly, the AT&T version only created 48-column cards instead of the standard 80-column card, but I was intent on copying the AT&T version, so if you ever look at the source you should change this line
int columns = 48;
So anyway I kind of forgot about it, but here we are, decades later.
Berkeley UNIX has continued to evolve, and a lot of the Berkeley code found its way into Linux, and MacOS, and even iOS.
Needless to say, iOS doesn’t actually include either the bcd or join programs, but it does include a lot of other Berkeley Unix code.
Apple lists the license agreement and credits for a ton of open source code in its Legal Notices section, and Berkeley, god bless them, has chosen to include the names of all these contributors from long ago. The Berkeley section says This code is derived from software contributed to Berkeley by …. and lists dozens of people, virtually all of whom did something way more important than I did.
But there it is. I’m sure hardly anybody reads the Legal Notices but it’s the first thing I check when there’s a new iOS release. Just making sure things are still there.
postscript
Berkeley unix mutated into OpenBSD and FreeBSD and NetBSD and Linux and MacOS and iOS and watchOS and tvOS and I can’t keep track of it all - but you can see the OpenBSD version of the BCD source here.
I am really amused that in my efforts to copy the AT&T version exactly, I inadvertently copied a bug from the original! Four years later, Dyane Bruce noticed (and fixed) that Q and R were being punched the same way! ooops.
Email from famous people
You might be wondering, “Why did you, Steve, send Jeff Bezos some jumper cables for his birthday in 2001?”
Amazon has a wish-list feature where you can list things you wanted other people to buy for you. And in 2001, Jeff Bezos had one, with jumper cables on it.
I figured, hey, I like Amazon, I’ll send the guy - who was not at the time the world’s richest man - some jumper cables, with a nice note saying “Happy Birthday, and I hope you never need these.”
(Meanwhile I created my own amazon wish list with some fancy stuff on it - I forget what exactly, some binoculars or something - because hey, you never know.)
And I actually got a gracious thank-you note from Jeff Bezos, thanking me for the jumper cables and agreeing that he too hoped he’d never need them. (He did not wind up buying me anything off of my own wish list, however.)
But somewhere in my email, I have a thank-you note from Jeff Bezos, which I will cherish forever, assuming I can ever find it
I have another email saying “Great idea - thanks.”
From Steve Jobs.
I really should find THAT one and frame it.